Managing Application Pool Identities
You can configure the identity under which worker processes in the application pool will run by assigning an account to the application pool. Application pool identity configuration is an important aspect of security in IIS 7.0, because it determines the identity of the worker process when the process is accessing resources. In IIS 5.0, the process runs under the LocalSystem account. That has significant security implications, because the user account has high access privileges. This changed in IIS 6.0 with the introduction of an application pool for which NetworkService is the default application pool identity. In IIS 7.0, the predefined worker process identities are the same as for IIS 6.0. Table 3 illustrates the built-in application identities in IIS 7.0.
Table 3. Built-In Application Pool Identities
On top of built-in accounts, you can create a custom user account to run the worker process in the context of the custom user account.
Security Account Changes in IIS 7.0
In IIS 7.0, both the anonymous user account (IUSR_computername) and IIS_WPG user groups have been removed and replaced by system built-in accounts rather than normal user and group accounts. Using a built-in predefined user Security Identifier (SID) ensures that the same common accounts exist in the remote IIS 7.0 computer. The built-in account initiative also eliminates the need to manage issues with user credentials, such as password expiration. The following built-in accounts are created during IIS 7.0 installation:
Note
IUSR_computername is created if the FTP Publishing Service (the legacy IIS 6.0 FTP) role service is installed in Windows Server 2008.
On top of the security user and user group account changes, IIS 7.0 introduces two additional enhancements related to application pool identity:
-
Application Pool Identity as Anonymous Account. Designate the application pool identity as the anonymous user account. (Simply set the userName in the anonymousAuthentication configuration section to be blank. ) The main advantage of configuring application pool identity as the anonymous user is that you do not have to manage security for a separate account.
-
Automatic IIS_IUSRS Membership. In IIS 6.0, when you configure custom application pool identity, the custom account must be a member of IIS_WPG, because this user group has preconfigured access permissions and rights to start the worker process. Similar access permissions and rights have been granted to the IIS_IUSRS user group in IIS 7.0. However, the custom account does not need to be explicitly added to the IIS_IUSRS group, because this is done implicitly by IIS 7.0. (The application pool identity is not actually added to the IIS_IUSRS group. The group SID is injected into the worker process token at run time, so it acts as a member of IIS_IUSRS. No changes to the local user database or Microsoft Active Directory directory service domain group membership are made.)
To revert to IIS 6.0 behavior, you can configure manual IIS_IUSRS group membership. This setting is per application pool, meaning that for the application pool with manual group membership, you will need to explicitly add the custom account to the IIS_IUSRS group. The following Appcmd syntax configures DefaultAppPool for manual IIS_IUSRS group membership.
appcmd set apppool "DefaultAppPool" /processModel.manualGroupMembership:True
Configuring Application Pool Identity
Although NetworkService is an account with reduced access privileges, you might change the worker process identity due to your business needs. For example, a security application might require access to system resources for which NetworkService does not have the necessary permissions. In this case, you can run the worker process from a custom account with necessary access rights
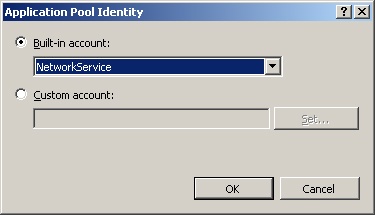
To use IIS Manager to configure application pool identity, expand the IIS computer node in the Connections pane and navigate to the Application Pools node. In the Application Pools display pane, select the application pool for which you want to change the identity account. Then click Advanced Settings in the Actions pane. In the Process Model section of the Advanced Settings dialog box, select the Identity property and then click the browse button (…) to display the Application Pool Identity dialog box, shown in Figure 3.
Caution
When changing the application pool identity, IIS 7.0 shuts down the current worker process if it is running and initiates a new worker process with the selected user identity. This impacts the availability of the application, and session details are lost during the application pool changes.
Use the following Appcmd syntax and the parameters shown in Table 4 to configure application pool identity.
appcmd set apppool ApppoolName /processModel.identityType:enum
/processModel.userName:string /processModel.password:string
Table 4. Syntax for Appcmd to Configure Application Pool Identity
The following example changes the default worker process identity from NetworkService to LocalService for the “Fabrikam Stock” application pool.
appcmd set apppool "Fabrikam Stock"
/processModel.identityType:LocalService
The identityType enumeration is case sensitive inside the configuration store. If you enter the correct value, Appcmd executes the command successfully and returns output like this.
APPPOOL object "Fabrikam Stock" changed
If you enter an incorrect value, you will see the following error messages.
ERROR ( message:Unknown attribute "identityType".. Reason: Enum must
be one of LocalSystem, LocalService, NetworkService, SpecificUser. )
To configure a custom application worker process identity, enter SpecificUser as the identityType attribute value. Then specify the user credentials by using the userName and password properties.
appcmd set apppool /apppool.name:"Fabrikam Stock"
/processModel.identityType:SpecificUser
/processModel.userName:"MyAppUsr"
/processModel.password:"passw@rd1"
The preceding example configures the MyAppUsr user account as the Fabrikam Stock application pool identity and specifies the account password as passw@rd1.
IIS updates changes in application pool identity in the <applicationPools> section in the applicationHost.config file. The element value includes the name of the application pool, the worker process model, and the process identity, if it is different from the default settings. The following shows the <applicationPools> configuration of the custom worker process identity configured for Fabrikam Stock application pool.
<applicationPools>
...
<add name="Fabrikam Stock" managedRuntimeVersion="V1.1"
managedPipelineMode="Classic">
<processModel identityType="SpecificUser" userName="MyAppUsr"
password="[enc:AesProvider:oGSyoej3RKswi3gsrYarpbMQrx0rVIY6nFHkPmjQAhE=
:enc]/>
</add>
...
</applicationPools>
- IIS 7.0 : Managing Application Pools (part 3) – Advanced Application Pool Configuration, Monitoring Application Pool Recycling Events
- IIS 7.0 : Managing Application Pools (part 1) – Application Pool Considerations, Adding a New Application Pool